A made-up illness stemming from a 2017 hoax has made it into Google's AI...
The US start-up Alsym Energy is currently developing a battery that is said to...
Heat pumps, a dealer platform, our own fintech – just three of several new...
Black Friday is almost here, which means it's an opportunity to take household cleaning...
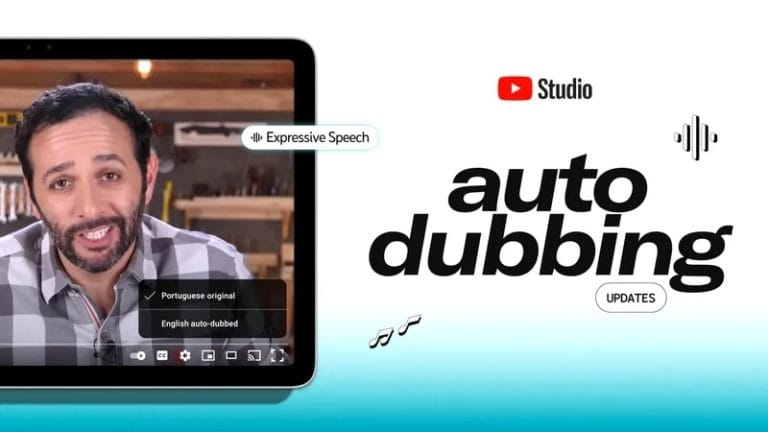
Anyone who uploads a video to YouTube will be able to have it automatically...
Content that fits the target group and can also be found – this is...
Is Amazon using its market power to manipulate prices on other platforms? Research by...
An AI chatbot gave tips in a Facebook group on how to prepare poisonous...
Page 1 of 11 Back Forward Tablets can be practical helpers in everyday life...
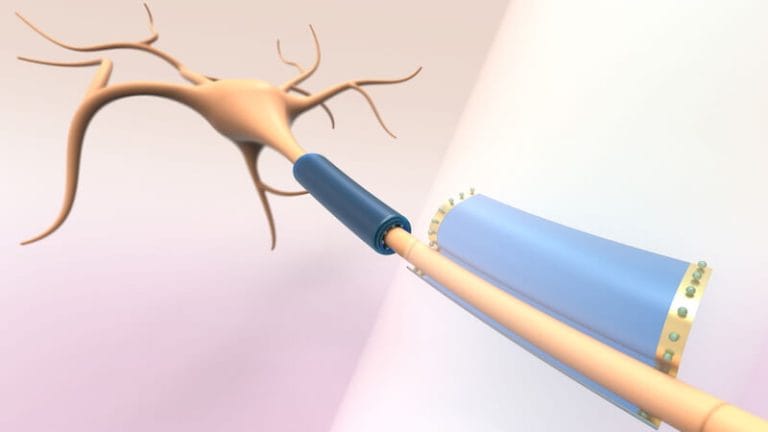
Researchers at the Massachusetts Institute of Technology (MIT) have developed tiny wearable devices that...