
Internet Protocol (IP) is a communication protocol used between all networked machines for forwarding data. Both in the TCP/IP Model and in the OSI Model, the important Internet protocol IP is in the layer called the network layer.
Operation
Data on an IP network that is sent in blocks referred to as files (the terms are basically synonymous in IP, being used for data at different locations in the IP layers). In particular, in IP no definition is needed before the node tries to send files to a node with which it has not communicated previously.
IP provides an unreliable (also called best effort) datagram (packet) service; that is, the package comes with almost no guarantees. The packet may arrive unordered (compared to other packets sent between the same nodes), it may also arrive in duplicates, or it may be lost entirely. If the application requires greater reliability, it is added at the transport layer.
Routers are used to forward IP datagrams across interconnected networks at the second layer. The lack of any guarantee of delivery means that the design of the exchange of packages is made more simplified. (Note that if the network drops, reorders, or otherwise damages a large number of packets, the performance observed by the user will be poor, so most network elements try hard not to do this sort of thing – best effort. However, a occasional error will have no noticeable effect.)
IP is the common element found in today’s public Internet. It is described in IETF RFC 791, which was first published in September 1981. This document describes the most popular network layer protocol currently in use. This version of the protocol is called version 4, or IPv4. IPv6 has 128-bit source and destination addressing, offering more addressing than IPv4’s 32-bit.
IPv4 Header Format
Version – The first header field of an IPv4 datagram is the version field, with four bits.
Header Size (IHL) – the second, four-bit field is the IHL (acronym for Internet Header Length) in number of 32-bit words (4 bytes) of the IPv4 header. As the IPv4 header provides the OPTIONS field that can be used to extend the IP header, the IHL field essentially specifies where exactly the header ends and the IPv4 datagram data begins. A minimum IPv4 header is twenty bytes long, so the minimum decimal value in the IHL field would be five, as follows:
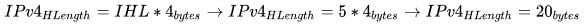
- Type of Service (ToS) – In RFC 791 , the next eight bits are allocated to a Type of Service (ToS) field , now DiffServ and ECN. The original intent was for a node to specify a preference for how datagrams could be handled as they travel through the network. For example, one node may set its ToS values field of IPv4 datagrams to prefer small time lag, while others may prefer high reliability. In practice, the ToS field has not been widely implemented. However, experimental, research and development work has focused on how to make use of these eight bits. These bits have been reset and more recently through the DiffServ working group at the IETF and by the code points ofExplicit Congestion Notification (ECN) ( RFC 3168. )
- Length (Packet) – The next sixteen-bit IPv4 field defines the entire length of the datagram, including header and data, in eight-bit bytes. The minimum size datagram is twenty bytes and the maximum is 64 Kb . The maximum datagram size any node requires to be able to handle is 576 bytes, but more modern nodes handle much larger packets. Sometimes subnets impose restrictions on size, in each case the datagrams have to be “fragmented”. Fragmentation is handled both at the node and at the packet switch in IPv4, and only at the node in the case of IPv6.
- Identifier – the next sixteen bit field is an identification field. This field is mainly used to identify identifying fragments of the original IP datagram. Some experimental work suggests using the IP field for other purposes, such as adding packets to carry the information to the datagram, in a way that helps to look up datagrams backwards with spoofed source addresses .
- Flags – the following three-bit field is used to control or identify fragments.
- Offset – The fragment offset field is thirteen bits long, and allows a receiver to determine the location of a particular fragment in the original IP datagram.
- Time to live (TTL) – an eight-bit field, TTL ( time to live) helps to prevent datagrams from persisting (ie running in circles) on a network. Historically, the TTL field limits the life of a datagram to seconds, but it has become a field for counting nodes walked. Each packet switch that a datagram traverses decrements the TTL field by one value. When the TTL field reaches zero, the packet is not followed by a packet switch and is discarded.
- Protocol – an eight-bit protocol field follows, defining the next protocol used in a data portion of an IP datagram. The Internet Assigned Numbers Authority maintains a list of protocol numbers. Common protocols and their decimal values include ICMP (1), TCP (6).
- Checksum – the next field is a checksum field for the IPv4 datagram header. A packet in transit is changed by each switch it traverses. One of these switches can compromise the packet, and checking is a simple way to detect header consistency. This value is adjusted along the way and checked at each new node. It only involves checking the header (not the data).
- Source address/Destination address – after the check field, the source and destination addresses, each 32 bits long, follow. Note that the source and destination IPv6 addresses are 128 bits each.
- Options – Additional header fields can follow the destination address field, but these are not normally used. Option fields can be followed by a path field which ensures that user data is aligned on a 32-bit word boundary. (In IPv6, the options move outside the standard header and are specified by the Next Protocol field , similar to the function of the “Protocol” field in IPv4).
The following are three examples of options that are implemented and supported on most routers:
- Security (specifies the security level of the datagram (used in military applications));
- Timestamp (Makes each router append its address and timestamp (32 bits), which serves to debug routing algorithms); and
- Record route (makes each router append its address).
IPv4 addressing and forwarding [ edit | edit source code ]
Perhaps the most complex aspects of IP are addressing and forwarding . Addressing defines how end node IP addresses are assigned and how subnets of node IP addresses are divided and grouped. IP forwarding is done by all nodes, but more commonly by network routers, which typically use the IGP or EGP protocols to help read IP datagrams that forward decisions across IPs on linked networks.
On the internet, and in the private networks that we see today in companies or even in homes, the communication protocol used by computers is called IP – an acronym for Internet Protocol. Created in the late 1970s, the IP protocol has as its “mission” not only to make two computers “talk”, but also to enable the interconnection of two or more separate networks. With very few exceptions, practically all the networks in the world ended up, in one way or another, being connected to each other and it was this communion of networks that ended up forming what we know today as the internet (name that, in Portuguese, can be translated as ” inter-networks” or “interconnected networks”).
The IP protocol has an addressing scheme similar to telephone numbers. Just as any telephone in the world is unique (considering the area code and country code), each computer connected to the internet has a unique number, which is called an IP address or IP number. This number is used to identify the computer on the internet. If you need to chat with someone over the internet, just send messages addressed to the IP address of the person’s computer.
For an email from Alice to leave her computer and reach Beto’s computer, for example, the data (in this case, the text of the email) must be divided into small packets (called IP packets) that are marked inside si the source IP address (that is, Alice’s computer’s unique number) and the destination IP (Beto’s computer’s unique number). The internet “turns around” to find its way between Alice and Bob, without either of them having to worry about it.
However, the IP protocol in its current version (version four, labeled IPv4) is already quite old and has many problems. The most serious are security flaws, which are periodically discovered and have no solution. Most attacks against computers on the internet today are only possible due to flaws in the IP protocol.The new generation of the IP protocol, IPv6, solves most of the security problems of the internet today, inherited from the antiquated project of IPv4.
But IPv4 has an even more pressing problem than its inherent insecurity: it has already exhausted its scalability. Every computer connected to the Internet – be it a personal computer, a workstation or a server that hosts a website – needs a unique address that identifies it on the network. IPv4 defines, among other important things for communication between computers, that the IP number has a 32-bit extension. At 32 bits, IPv4 theoretically has around four billion IP addresses available, but in practice, what is actually available is less than half of that. If we count that the planet has six billion inhabitants and that each device connected to the internet (which includes smartphones, PCs, notebooks and the like) needs a number of its own, it is easy to see that the account does not close. This number, being finite, one day ends.
On top of that, IP addresses are “locked in” geographically. Two nearby addresses are necessarily in the same city or region. Considering that about three-quarters of the IP addresses available to the internet are located in the United States (even if never used), there are just over a billion addresses left for the rest of the world – further adding to the shortage problem.
The entry of smartphones and other mobile devices (which are cheap and extremely popular) on the internet has contributed to the number of available IP addresses being even more scarce. In fact, some pessimistic predictions were that IP addresses would run out completely in 2012 , turning the internet into real chaos .
The advent of IPv6, with 128 bits, would solve all these problems. First, because it eliminates virtually all known IPv4 security holes, making communications vastly more secure. IPv6 is likely to be a massive headache for criminal hackers.
Second, IPv6 defines 128 bits for addressing, and therefore has about 3.4 × 10^38 addresses available (or 340 followed by 36 zeros). For those who don’t want to do the math, just know that there are many billions of quadrillion addresses available, guaranteeing that there will be no shortage of IP numbers for humans for millennia.
According to the initial draft of a document proposed by the IETF – Internet Engineering Task Force, the body responsible for the technological development of the Internet, the migration from IPv4 to IPv6 should have started sometime between 2009 and 2010, with full migration by the end of 2011. The schedule is still delayed due to the various problems of the complete conversion. Google , Yahoo! and Facebook are already starting to adopt IPv6.


