As a self-employed person, you are happy about every bargain. Are you looking for...
Large data centers consume huge amounts of energy. But the Swiss start-up FinalSpark wants...
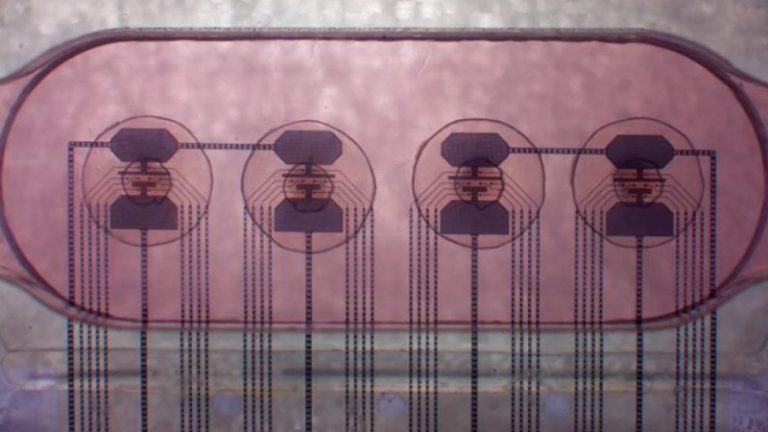
A team of researchers recently made progress in the production of so-called quantum dot...
Researchers from the USA have developed a new AI system that allows people wearing...
In the “Homescreen!” series, we regularly present you the home screens of people from...
Sebastian Becker is General Partner at the Zurich-based VC Redalpine. Redalpine Redalpine looks at...
Can people tell whether images, text or audio files were created by humans or...
Camping is very popular in Germany. Many people therefore buy a motorhome or camper...
Researchers at MIT could bring about a logistics revolution. The goal: hundreds of automated...
Page 1 of 11 Back Forward Whether off-road or in the city: many Germans...