Amazon has put a new data center into operation for its web service. It...
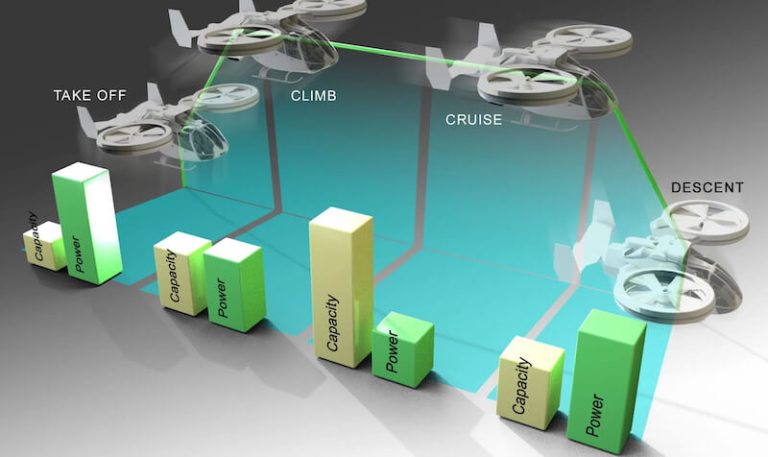
Researchers at Oak Ridge National Laboratory have been working on developing so-called eVTOL batteries...
Are you tired of having all your tariffs spread across multiple providers? With one...
Page 1 of 11 Back Forward Cars are generally considered safe in Germany. However,...
With solar systems for the balcony, consumers can generate their own electricity and use...
Who is really building AI – and who is just pretending?Give her A contribution...
There is no legal basis for unreasonable and unfounded data retention and surveillance of...
Developments in artificial intelligence are keeping the job market quite busy. But what impact...
The Greentech Festival 2024 will take place under the motto “Accelerating Change from Berlin”....
Mona Gindler has been at Senovo for around five years. The Munich-based woman has...