The trend continues towards balcony power stations, because it has never been easier to...
This summer, O2 is offering the “Unlimited on Demand” offer for the price of...
AI image generators are usually available online free of charge. With these tools, hobby...
The founders are part of the German startup establishment and after 12 years they...
Wind energy plays a key role in reducing CO2 emissions. It offers an environmentally...
You can't live without a cell phone. Whether at work or in your private...
The volume of VC investments made in Europe is increasing again. Which funds are...
The volume of VC investments made in Europe is increasing again. Which funds are...
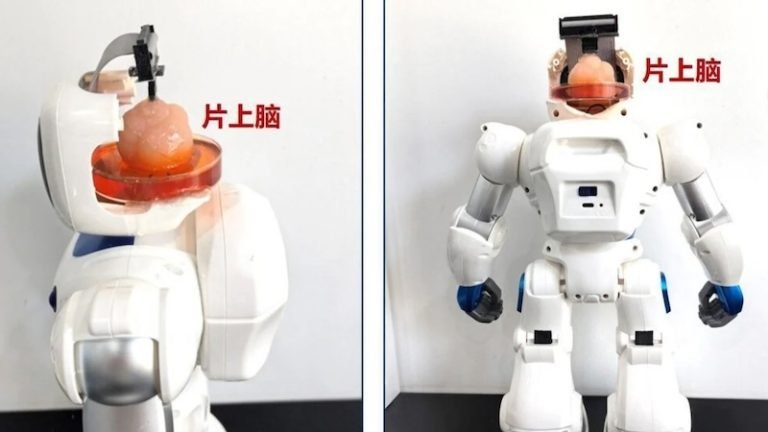
Chinese researchers have built a robot and given it a brain made of human...
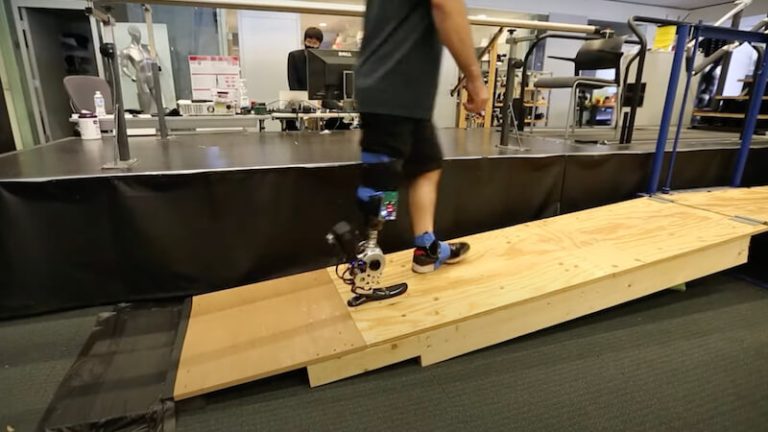
A neural interface allows people to control a new type of prosthesis using their...