
Reports and background information on the topic of cyber security – from IT security and security & compliance to identity & access to data protection / EU GDPR
In the digital age, huge amounts of publicly accessible data are generated every day. Drawing the right information and insights from this huge amount of data has great potential, but at the same time is a great challenge. Here…

Every action on an information technology system such as a computer leaves traces. From these traces, forensics experts can draw conclusions about activities on the computer or IT system and thus solve crimes such as hacker attacks or malware infections. How to go…
Like other public institutions, the Bundeswehr is continuously modernizing its IT landscape in order to meet current and future challenges, accelerate processes and ensure collaboration nationally and internationally. A variety of projects and programs from the past…

From now on, we would like to regularly inform you about current aspects of the digital transformation of public administration and our administrative projects with our Public Sector topic specials. The first special focuses on the Online Access Act (OZG), which…

The flexibilization and acceleration in the use and provision of IT services and information resources presents cyber security with new challenges. Options such as “Bring your own device” (BYOD), “Mobile working” and the use of cloud…

The EU General Data Protection Regulation (EU GDPR) ensures EU-wide and, above all, stricter data protection guidelines than were previously the case. Many companies have now taken a number of measures to adapt their processes to the new…

CONET offers companies practical workshops and advice to review and further optimize the EU GDPR measures they have taken. As part of such a workshop, the CONET experts analyzed the existing…
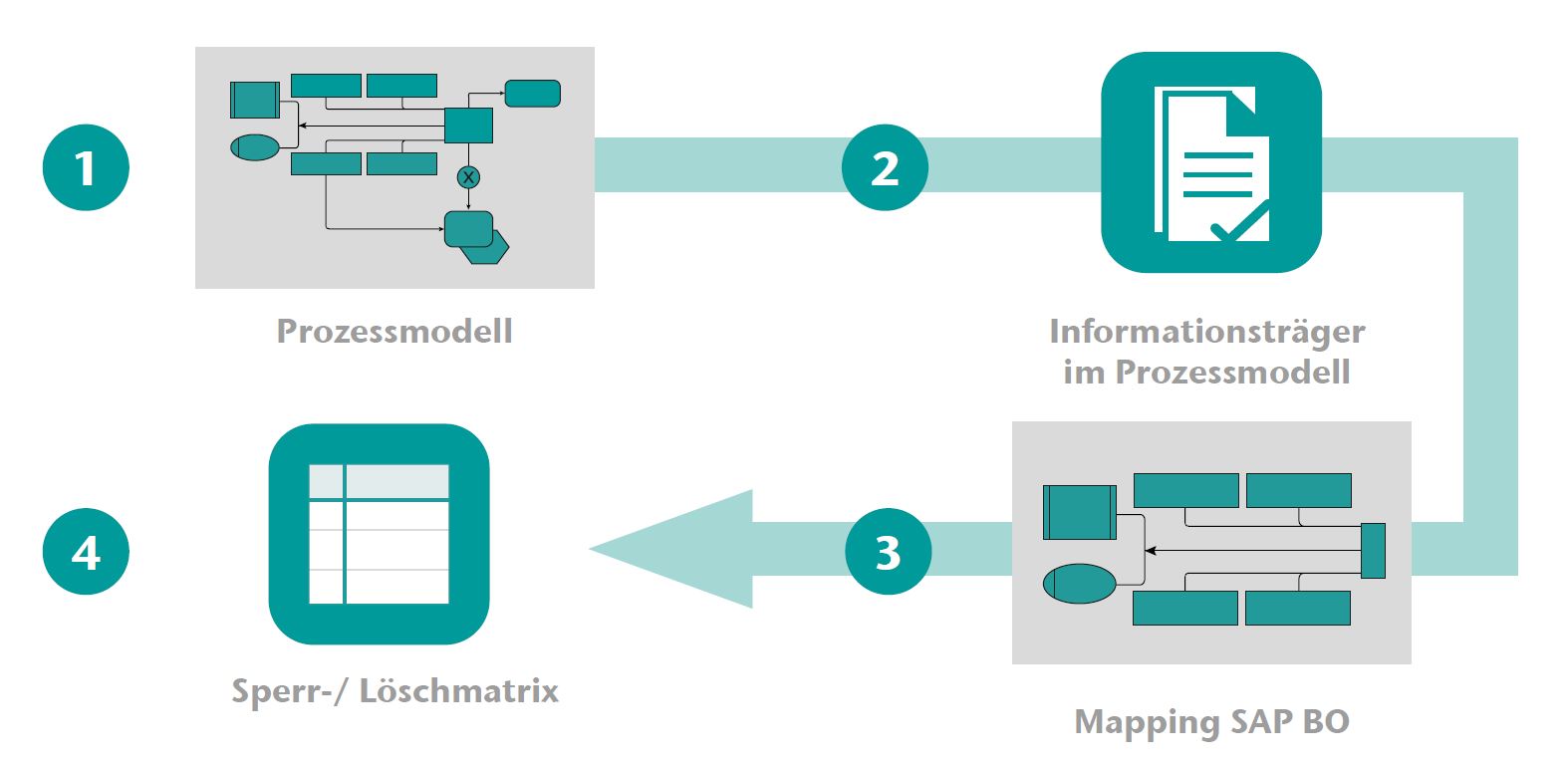
The Federal Agency for Real Estate Tasks (BImA) is working on the implementation of the European General Data Protection Regulation (EU-GDPR) with conceptual and technical support from the IT system and consulting company CONET in process analysis and process documentation.

The security of emails must fundamentally be viewed from two completely different perspectives: the security of the content as well as the security of the transmission and the guarantee of integrity. This article is intended to provide an overview of…
Source: https://www.conet.de/blog/category/loesungen/cyber-security/


